We recently replaced our existing router with a Meraki MX65w Security Appliance. While Meraki does have multi-factor authentication to log into the cloud controller, we were disappointed to find out that they do not have multi-factor authentication for client VPN. However, there are third-party solutions that can be used to provide multi-factor authentication for client VPN. These third-party solutions can be found on Meraki’s website below.
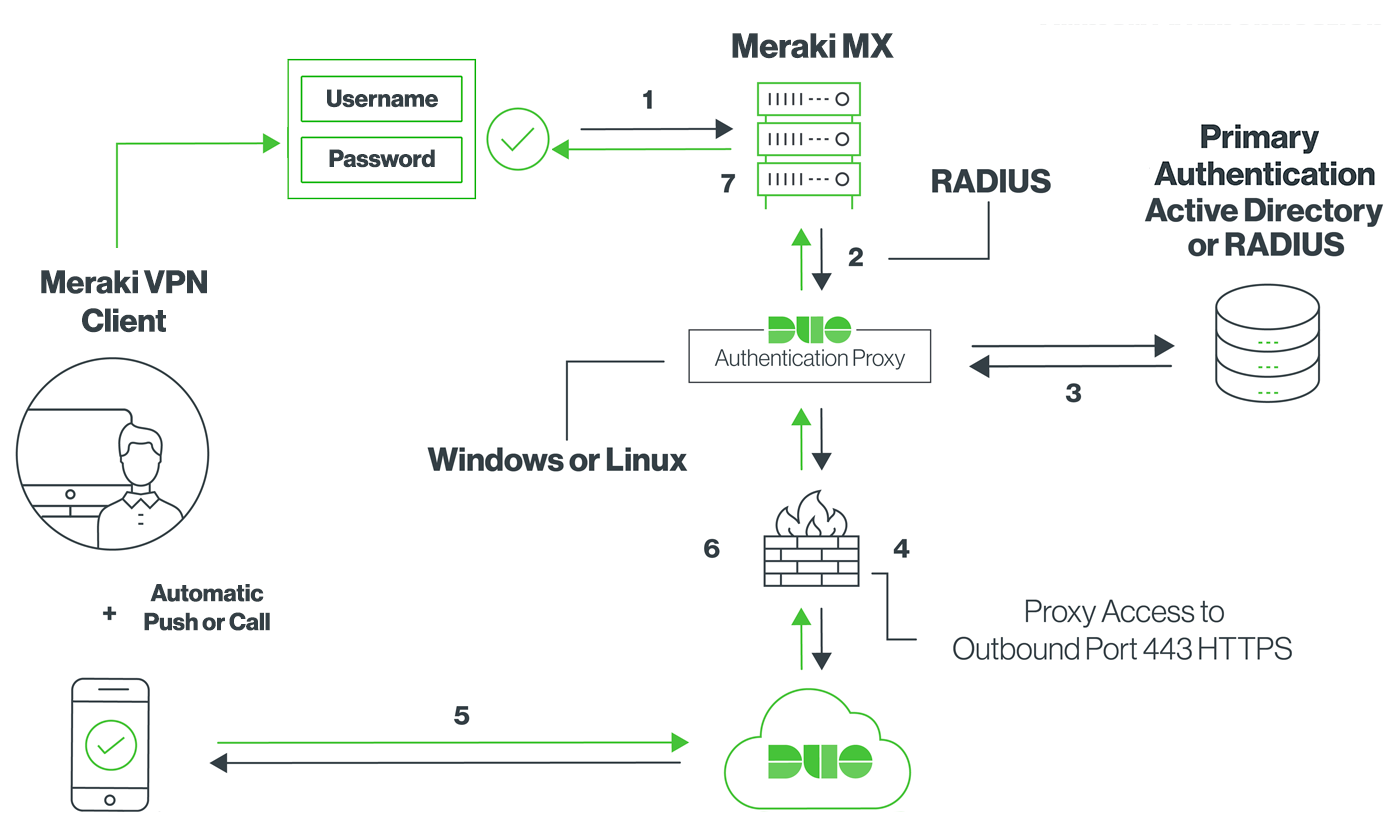
We are currently using a Meraki MX84 for VPN. It connects to our Active Directory to authenticate users. I am setting up a Duo Authentication Proxy to tie into my Meraki MX84 so I can have Multi-Factor Authentication on my VPN. The Duo Auth Proxy is asking for a Radius Secret from the Meraki. Duo integrates with your Meraki Client VPN to add two-factor authentication to any VPN login. Background - Client using Meraki Client VPN with DUO, works fine. Client wants to add a new VLAN/Subnet then all of a sudden DUO stops authentication with the new Subnet 'IN VPN'. If you don't add the new VLAN/Subnet into the VPN it works fine. Meraki Client VPN uses the Password Authentication Protocol (PAP) to transmit and authenticate credentials. PAP authentication is always transmitted inside an IPsec tunnel between the client device and the MX security appliance using strong encryption. User credentials are never transmitted in clear text over the WAN or the LAN.
We chose to use Windows Azure Multi-Factor Authentication (Azure MFA) Server. The Azure MFA Server is installed on a Windows 2012 Server acting as a Domain Controller. Unfortunately, the set-up and configuration of Azure MFA with Meraki Security Appliance is not well documented. Below are some useful tips from our experience with setting this up.
- By default, the Client VPN timeout on the Meraki Security Appliances is 15 seconds. For there to be enough time for the authentication to complete this must be extended. To extend this you will have to open a support case via the Meraki dashboard and ask to have it extended. Azure recommends this being at least 60 seconds.
- Logging is very important. Both the Meraki Security Appliance and the Azure MFA server have the capability to configure syslogs. This is very useful as it shows the communication between the two devices and can help pinpoint where the issue lies. Below is a copy of our logs once we had this set-up properly.
Duo Meraki Vpn Reviews
Meraki Vpn Azure Mfa
- Be persistent and know when to walk away and take a break.
Duo Meraki Vpn Chrome
Hope these tips help!
